In order to login to the VMsliver created as part of a FABRIC slice you must utilize a so-called bastion host (aka ‘hop node’ or ‘jump host’).
The purpose of the bastion hosts is two-fold:
- Provide better facility security by limiting which IP addresses are allowed to contact your VM sliver from the public Internet.
- Help bridge IPv4 users to IPv6 sites and vice versa. Many of the FABRIC sites provide only IPv6 addressable VMs which are unreachable for users coming from IPv4 providers. Since FABRIC bastion hosts are dual-stacked (support both IPv4 and IPv6), this problem goes away
As a result, unlike other environments or testbeds you may have encountered, at least two SSH keypairs are used in FABRIC:
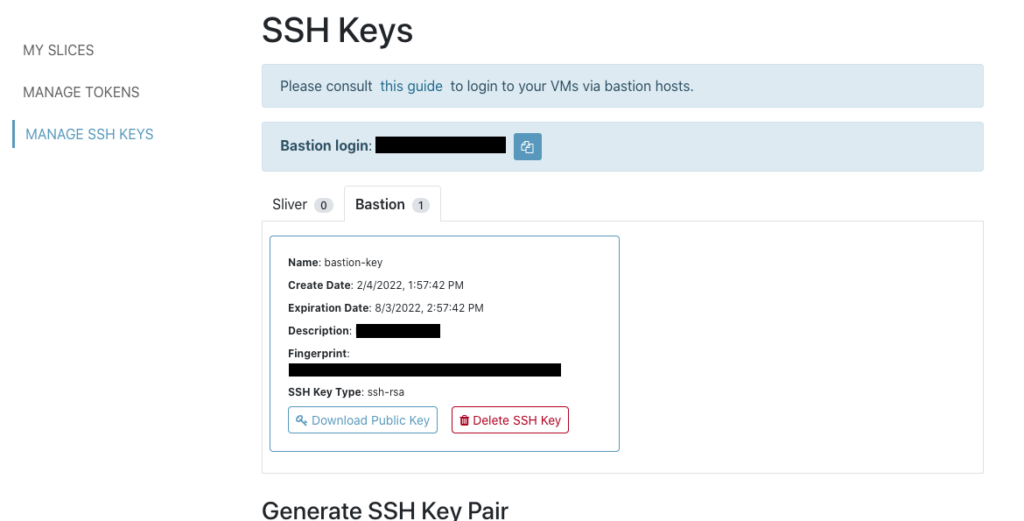
- Your ‘bastion’ keypair – this keypair requires rotation, i.e. the keypair has a finite lifetime before it needs to be renewed. The public key of this keypair is stored on the bastion hosts and allows you to ‘hop’ over them into your VM slivers. FABRIC will automatically ‘expire’ this public key and remove it from the bastion host, so you have to periodically generate a new keypair and have the public key uploaded to the bastion hosts.
- Your ‘sliver’ keypairs – these keypairs are long lived. The public key of these keypairs is installed into your VM slivers by FABRIC control framework when you create them. You can use multiple keypairs to login to e.g. VMs in different slices, but below we assume you just have one such keypair.
Notice that you and only you are in the possession of private keys within those keypairs – if you lose them, the keypairs must be regenerated. Even if you use FABRIC portal to generate a keypair, the portal allows you to download your private key, but does not store it. FABRIC only stores the public keys.
In addition there are two usernames involved – one on the bastion host and one in the VM sliver.
- The one used for the bastion host is part of your FABRIC identity and can be found in the portal (see figure below).
- The one used in the VM sliver typically depends on the image you chose to load and for many cloud-ready images defaults to
ubuntuorcentosdepending on the distribution you are using.
Both the Portal and Jupyter Notebooks show you exactly the SSH command you need to issue to login to each VM, including its IP address, and the VM image username. Your bastion user name is normally part of your SSH configuration file.
Other useful articles on this topic:
